 Over half of the 30,000 investigated Android Apps are leaking secrets that could have huge repercussions for both app developers and their customers.
Over half of the 30,000 investigated Android Apps are leaking secrets that could have huge repercussions for both app developers and their customers.New research by Cybernews shows that thousands of apps have hard-coded secrets. This means that a malicious actor (and not necessarily a very skilled one) could gain access to API keys, Google Storage buckets, and unprotected databases and eventually exploit that information for their benefit simply by analyzing publicly available information about apps.
As if that wasn’t enough, Cybernews found dozens of malicious apps on the Google App Store and a logic hole in Google’s services, leaving Android users vulnerable to malware infections.
“Hardcoding sensitive data into the client-side of an Android app is a bad idea. In most cases, it can be easily accessed through reverse-engineering,” Cybernews researcher Vincentas Baubonis said.
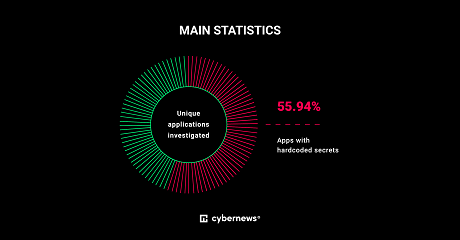 Leaky apps
Leaky appsThe research team investigated 42,799 applications from the Google Play Store and was able to download 33,334 of the initially identified apps, including approximately 6,000 most popular ones.
The team could not extract secrets from 9,465 initially identified target apps because of regional limitations for downloads, corrupt archives downloaded, or obfuscation of app code.
However, after a month-long investigation of over 30,000 apps, the researchers came to a few important conclusions. First, a great scale of data can be analyzed with what Baubonis called mediocre infrastructure in just a few weeks. A persistent threat actor with more advanced tools could extract more secrets in a shorter period and then use them for malicious purposes.
Second, 55.94% (18,647) apps have hard-coded secrets, including different API (application programming interface) keys and even links to open databases exposing sensitive corporate and user data.
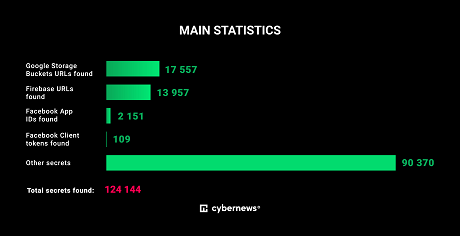
In total, researchers found over 124,000 strings potentially leaking sensitive data. Less than half of the analyzed apps didn’t have secrets hard-coded within the app.
Twenty-two unique types of secrets were discovered, with various API keys, open Firebase datasets, and links to Google Storage buckets being the most sensitive ones.
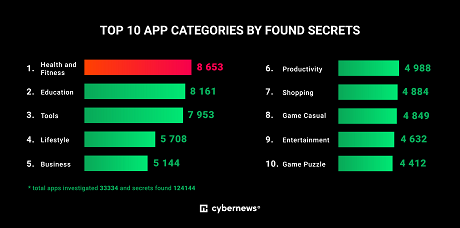
We found the most hard-coded secrets in apps within these five categories: health and fitness, education, tools, lifestyle, and business.
 Open databases
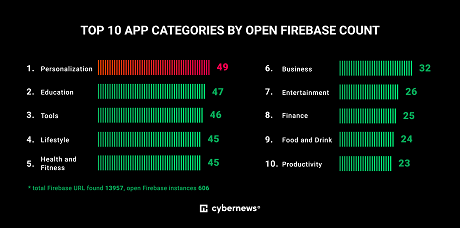
Open databasesAfter analyzing the data, researchers found over 14,000 Firebase URLs, and 606 were links to open Firebase instances.
Essentially, Firebase is a JSON database that stores either public or private information of an application or its users. It is the most popular storage solution for Android apps.
Google also provides this service, so application developers wouldn’t have to worry about setting up and maintaining their databases. Sometimes, misconfiguration of these databases leads to data leaks when the Firebases are left open for public access.
The following five categories have the highest percentage of open Firebase instances: personalization (14.76%,) video players (12.86%,) parenting (10.53%,) libraries and demo (10.00%,) and game and music (9.09%.)
 Google’s logic flaw
Google’s logic flawThe comprehensive research of Android Apps also led our team to the discovery of a basic logic flaw in Google cloud services.
It seems that users can download an app from the Play Store without getting any warning or notification that it might be malicious.
The Cybernews research team downloaded apps directly from the Google Play Store to one computer. For a proper analysis, the team had to upload those apps to Google Drive and download them on another computer.
However, when our researchers tried to download some of the apps from Google Drive, Google warned about their potential dangers, and APK (Android Package Kit) couldn’t even be executed without some type of emulation/virtual environment.
Out of over 33,000 apps, researchers couldn’t download 44 apps from Google Drive even though they didn’t have any problems downloading them straight from the Play Store.
Given the team analyzed only 33,000 apps out of 3,5 million that the App Store has, it is likely that many more malicious applications can be downloaded via an official app distribution channel.
Google storage bucketsOur research team also found 17,557 Google Cloud Storage (GCS) buckets – links to storage where anything from text files to images and videos can be stored.
If left open, a threat actor could read and write any information within it. Most commonly, security misconfigurations occur during the setup when the bucket is left open for anyone with an internet connection or any authenticated Google user.
The highest number of GCS buckets was discovered within these five categories: health and fitness (1205,) education (1168,) tools (1135,) lifestyle (794,) and business (726.)
Facebook problemCybernews researchers discover 109 Facebook Client tokens and 2151 Facebook App IDs. App IDs, coupled with client tokens, let you create an account within the app by using Facebook as an OAuth (open authorization) service, used to grant websites and applications access to user data without them having to share passwords.
With both of these keys accessible and a bunch of bot Facebook accounts, one can easily spam the application with a ridiculously large number of users, thus disrupting its normal activity and causing a denial of service.
The majority of Facebook IDs were discovered in these categories: health and fitness (246,) shopping (146,) lifestyle (121,) game casual (104,) and puzzle games (87.) The highest number of client tokens was found in shopping, strategic games, health and fitness, finance, and entertainment categories.
Accessible API keysAll the categories the team looked into store hard-coded application programming interface (API) keys. Generally, API keys are used for authentication purposes to allow apps to recognize individual users and vice versa. Storing API keys can lead to security issues if a threat actor finds a way to access them.
Most commonly, Google API keys are hardcoded within the apps. In total, our team discovered 17,767 Google API keys.
It is not uncommon to leave API information accessible, especially with APIs that do not store sensitive data. However, even that is not recommended as an accessible API could affect the application's overall performance.
Our team also discovered some internal APIs hardcoded within the apps, too. They are usually extremely sensitive and should not be left for public access.
Earlier this year, Cybernews ran
a story that is a shining example of how dangerous leaving the admin key in the application's front end might be. Service providers using Onfido, an identification verification (IDV) service, exposed an API token, leaving millions of customers of large businesses, such as Europcar, vulnerable to identity theft.
Recently, cybersecurity firm CloudSEK
discovered 3,207 apps leaking Twitter API keys. By making use of them, threat actors could access and even take over Twitter accounts and build bot armies serving various purposes, such as disinformation or cryptocurrency scams.
source